
ISO/IEC 15944-8:2012(en), Information technology — Business Operational View — Part 8: Identification of privacy protection requirements as external constraints on business transactions

The Use of Legal Ontologies in the Development of a System for Continuous Assurance of Privacy Policy Compliance * Bonnie W. Morris, Ph.D. CPA Division. - ppt download

ISO/IEC 15944-12:2020(en), Information technology — Business operational view — Part 12: Privacy protection requirements (PPR) on information life cycle management (ILCM) and EDI of personal information (PI)

CAMLearn: Une Architecture de Système de Recommandation Sémantique Sensible au Contexte. Application au Domaine du M-Learning. (CAMLearn: A Context-Aware Mobile Learning Recommender System. Application to M-Learning Domain) | Semantic Scholar
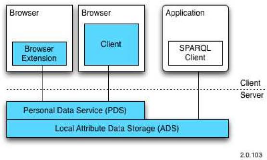
Memoire Online - La protection de la vie privée dans un système de gestion d'identité - Bahmed et Hassane Boumriga
![How] Can Pluralist Approaches to Computational Cognitive Modeling of Human Needs and Values Save our Democracies? - Persée How] Can Pluralist Approaches to Computational Cognitive Modeling of Human Needs and Values Save our Democracies? - Persée](https://www.persee.fr/renderIssueCoverThumbnail/intel_0769-4113_2019_num_70_1.jpg)
How] Can Pluralist Approaches to Computational Cognitive Modeling of Human Needs and Values Save our Democracies? - Persée

PDF) Analyse de la sécurité et de la protection de la vie privée des systèmes de gestion d'identités






![PDF] A Meta-model for Inferring Inter-theory Relationships of Causal Theories | Semantic Scholar PDF] A Meta-model for Inferring Inter-theory Relationships of Causal Theories | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/a06c9092b46c815805b80c2a42cc192a6a367475/6-Figure10-1.png)






![PDF] A Meta-model for Inferring Inter-theory Relationships of Causal Theories | Semantic Scholar PDF] A Meta-model for Inferring Inter-theory Relationships of Causal Theories | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/a06c9092b46c815805b80c2a42cc192a6a367475/2-Table1-1.png)
![PDF] A Meta-model for Inferring Inter-theory Relationships of Causal Theories | Semantic Scholar PDF] A Meta-model for Inferring Inter-theory Relationships of Causal Theories | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/a06c9092b46c815805b80c2a42cc192a6a367475/6-Figure9-1.png)

